Table of Contents
LDAP
Overview
The goal of the LDAP synchronization module is to apply a nearly random group- and user structure from an LDAP-service and to feed it with necessary information in order to use this as a basis for the TIM group-/ user structure. The foundation for this module constitutes the TimedService component via which the synchronization is run time-controlled.
The module consists of two essential parts which together allow a synchronization of naerly random LDAP-structures. In order to establish an LDAP-module several steps are necessary which are explained in this entry.
ATTENTION! These settings and methods should only be applied by experienced users.
Basic configuration LDAP
In order to enable TIM to access to an LDAP-server, the following file has to be adapted:
jboss<version>\standalon\configuration\tim-ldap.properties
These settings apply for all clients! For a detailed description of the single lines you can get further information here: here
Test LDAP connection
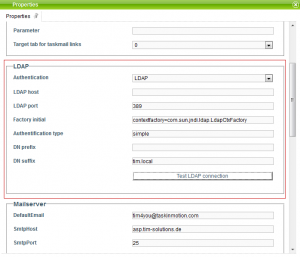 In order to test elemental LDAP connections, some settings have to be applied in the [client_profile|Clientprofil]]. For this, the following merits are required:
In order to test elemental LDAP connections, some settings have to be applied in the [client_profile|Clientprofil]]. For this, the following merits are required:
| Authentication | Can stay empty |
|---|---|
| LDAP-Host | Host or IP of the LDAP server |
| LDAP-Port | Port which the LDAP server responds to (Standard 389) |
| Factory Initial | Must contain the following merit “com.sun.jndi.ldap.LdapCtxFactory” |
| Kind of authentication | Can be “simple” or “digest-md5” (Standard “simple”) |
| DNS Prefix | Can stay empty |
| DNS Suffix | Here, the DNS suffix of the firm has to be deposited |
Afterwards an LDAP-lookup can be initiated via the button “Test LDAP connection”. For this you simply enter an LDAP user and password.
ATTENTION! The password is displayed in clear text!
Establish an LDAP lookup
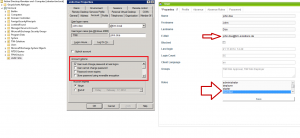 LDAP lookup means tthat TIM forwards authentication requests to the LDAP server and inquires if the user has the right to register himself. As the rights management is currently deposited in TIM, the user has to be registered in TIM!
LDAP lookup means tthat TIM forwards authentication requests to the LDAP server and inquires if the user has the right to register himself. As the rights management is currently deposited in TIM, the user has to be registered in TIM!
IMPORTANT! (see screenshot)An e-mail address has to be deposited in the Userprofil
The log-in is not permitted as long as the user has to change his password in the AD
The rights of the user are managed in TIM
LDAP Sync
The LDAP Sync givs the possibility to create users in TIM and to apply attributes from the LDAP. How LDAP attributes are linked to TIM-attributes can be looked up in the following page.
In order to activate the LDAP-Sync, the the following timer is required.
Example in practice
Such a group structure and the configuration of 4 timers (one timer per group) enables the admin to conviniently allocate rights in TIM. Important is that all TIM-users are in the group TIM-Member. If this is not given, it could leat to an admin not being able to open a smartform as the member-right is required. 
